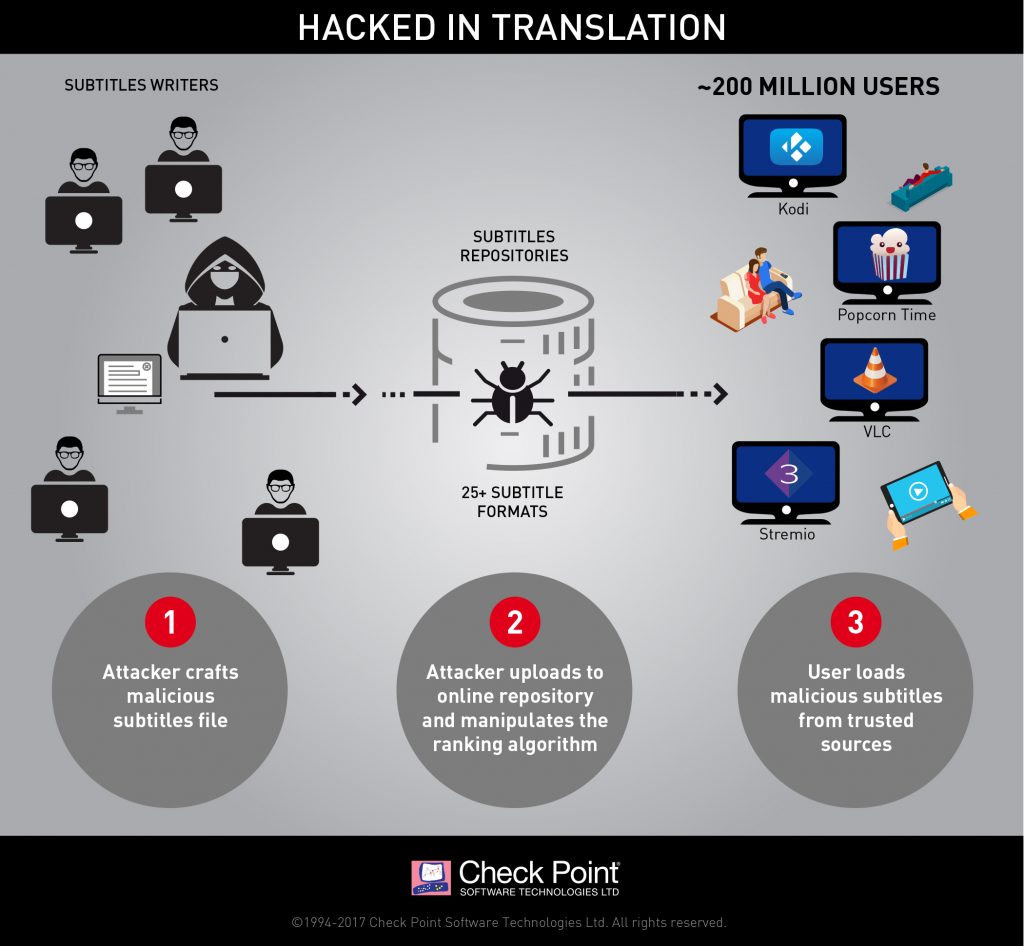
Check Points estimates there are approximately 200 million video players and streamers that currently run the vulnerable software, making this one of the most widespread, easily accessed and zero-resistance vulnerability reported in recent years.
VLC has over 186 million downloads of its version 2.2.4 alone, which was released June 5, 2016. Kodi (XBMC) has reached over 10 million unique users per day, and nearly 40 million unique users each month.
VLC Hack Description
For VLC players, it uses a ParseJSS Null Skip Subtitle Remote Code Execution hijack.
A remote code execution vulnerability exists in VLC Subtitles mechanism. The vulnerability is due to the way VLC parses subtitle files. Successful exploitation could result in arbitrary code execution on the client machine. In the demo video below we see the subtitles essentially activating a TinyVNC connection with the attackers machine, allowing full access for the desktop.
Action
Download now.
Platforms affected
Check all platforms affected at and update
http://blog.checkpoint.com/2017/05/23/hacked-in-translation/
Proof-of-Concept video of a remote hacker taking over your desktop
No comments:
Post a Comment