Windows 10 has an unprecedented level of privacy controls. Unlike other companies, you can opt out of many of privacy settings. If you want to go the extra mile, check the last two URLs.
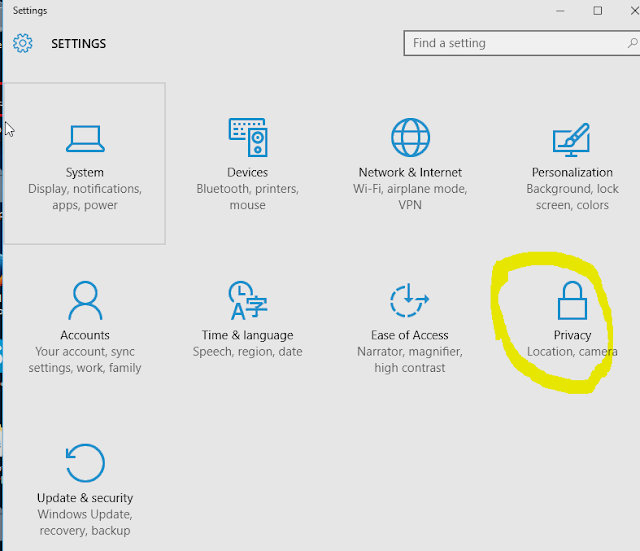
In Windows 10 - goto ‘Settings’ -> ‘Privacy’. It may seem like allot of options, but all 13 different sections you have a choice to control your privacy setting.
Turning everything of your concern to ‘off’.
One last thing you can turn of adds in your browser by opt out of personalized ads from Microsoft here
https://choice.microsoft.com/en-US/opt-out
http://lifehacker.com/what-windows-10s-privacy-nightmare-settings-actually-1722267229
To go the extra level you can turn all of these off;
All text typed on the keyboard is stored in temporary files, and sent (once per 30 mins) to:
- oca.telemetry.microsoft.com.nsatc.net
pre.footprintpredict.com
reports.wes.df.telemetry.microsoft.com
This will allow Microsoft and the greater Jewish community to have a way to steal every joke, every poem, every intellectual endeavor you ever create and have it copyrighted before you even stop typing.
Telemetry is sent once per 5 minutes, to:
- vortex.data.microsoft.com
vortex-win.data.microsoft.com
telecommand.telemetry.microsoft.com
telecommand.telemetry.microsoft.com.nsatc.net
oca.telemetry.microsoft.com
oca.telemetry.microsoft.com.nsatc.net
sqm.telemetry.microsoft.com
sqm.telemetry.microsoft.com.nsatc.net
This allows them to track you very accurately.
Typing the name of any popular movie into your local file search starts a telemetry process that indexes all media files on your computer and transmits them to:
- df.telemetry.microsoft.com
reports.wes.df.telemetry.microsoft.com
cs1.wpc.v0cdn.net
vortex-sandbox.data.microsoft.com
pre.footprintpredict.com
This allows them to index any “unauthorized” content, and build a dossier on you that can be used in conjunction with their tracking data to stuff almost anyone in jail when needed.
When a webcam is first enabled, ~35mb of data gets immediately transmitted to:
- oca.telemetry.microsoft.com
oca.telemetry.microsoft.com.nsatc.net
vortex-sandbox.data.microsoft.com
i1.services.social.microsoft.com
i1.services.social.microsoft.com.nsatc.net
This allows them to get a good layout of your home and surroundings, and a good look at YOU PERSONALLY so they know exactly who to go get and how to stage the attack when something you typed pissed them off.
Everything that is said into an enabled microphone is immediately transmitted to:
- oca.telemetry.microsoft.com
oca.telemetry.microsoft.com.nsatc.net
vortex-sandbox.data.microsoft.com
pre.footprintpredict.com
i1.services.social.microsoft.com
i1.services.social.microsoft.com.nsatc.net
telemetry.appex.bing.net
telemetry.urs.microsoft.com
cs1.wpc.v0cdn.net
statsfe1.ws.microsoft.com
If this weren’t bad enough, this behavior still happens when Cortana (microsoft’s version of SIRI) is not installed.
Add these entries to your hosts file to block these addresses.
| 127.0.0.1 df.telemetry.microsoft.com
127.0.0.1 reports.wes.df.telemetry.microsoft.com
127.0.0.1 cs1.wpc.v0cdn.net
127.0.0.1 vortex-sandbox.data.microsoft.com
127.0.0.1 pre.footprintpredict.com
127.0.0.1 oca.telemetry.microsoft.com
127.0.0.1 oca.telemetry.microsoft.com.nsatc.net
127.0.0.1 vortex-sandbox.data.microsoft.com
127.0.0.1 pre.footprintpredict.com
127.0.0.1 i1.services.social.microsoft.com
127.0.0.1 i1.services.social.microsoft.com.nsatc.net
127.0.0.1 telemetry.appex.bing.net
127.0.0.1 telemetry.urs.microsoft.com
127.0.0.1 cs1.wpc.v0cdn.net
127.0.0.1 statsfe1.ws.microsoft.com
127.0.0.1 vortex.data.microsoft.com
127.0.0.1 vortex-win.data.microsoft.com
127.0.0.1 telecommand.telemetry.microsoft.com
127.0.0.1 telecommand.telemetry.microsoft.com.nsatc.net
127.0.0.1 oca.telemetry.microsoft.com
127.0.0.1 oca.telemetry.microsoft.com.nsatc.net
127.0.0.1 sqm.telemetry.microsoft.com
127.0.0.1 sqm.telemetry.microsoft.com.nsatc.net
|
Update Nov 3, 2016
From
https://www.ghacks.net/2016/11/23/microsoft-gives-third-parties-access-to-windows-10-telemetry-data/?PageSpeed=noscript
but the article seems to contradict itself.
Microsoft struck a deal with security company FireEye recently according to a report on Australian news magazin Arn which gives FireEye access to all Windows 10 Telemetry data.
Update: Microsoft told
Betanews that it is not sharing Windows 10 Telemetry data with the company.
The nature of the deal between Microsoft and FireEye is to license threat intelligence content from FireEye iSIGHT Intelligence. This additional layer of intelligence includes indicators and reports of past attacks collected and edited by FireEye and enhances detection capabilities of Windows Defender Advanced Threat Protection (WDATP). The deal does not include the sharing of Microsoft telemetry.
The report states that FireEye in return will provide Microsoft with the company's
iSIGHT Intelligence software for Windows Defender Advanced Threat Protection on Windows 10 devices.
FireEye iSIGHT Intelligence is a proactive, forward-looking means of qualifying threats poised to disrupt business based on the intents, tools and tactics of the attacker.
Windows Defender is built-in to Windows 10 and enabled by default unless other security software is recognized by the operating system.
Pro and Enterprise customers
may upgrade to Windows Defender Advanced Threat Protection featuring endpoint behavioral sensors, cloud security analysis and threat intelligence.
The news article suggests that the partnership benefits Microsoft, and specifically the reputation and credibility of the commercial version of Windows Defender.
A press release
by FireEye on November 3, 2016 provides additional details on the deal. The company's iSIGHT Intelligence software is available through Windows Defender Advanced Threat Protection (WDATP) but not the free version of Windows Defender.