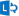I recently been using Bitly to shorten URLs from Microsoft Onedrive, and I noticed today that the shortened URL looked different.
Looks like the Microsoft URL Shortening is now active, in partnership with Bitly which has been rumored for awhile now.
For example, this OneDrive URL
shortened to a cute domain of 1drv.ms
For those that don't know, the Bitly default domain name is bit.ly
but this URL works as well.
So its solutions seems to be an URL domain alias.
NY Times uses Bit.ly as well (still working in 2017)
https://nyti.ms/2jHV1mn
https://bit.ly/2jHV1mn
17-Jan-17 Update
Microsoft apparently did not like this reverse engineering of its shortening service and now produces this obscure link
https://1drv.ms/i/s!AvOyviiXZJmPlSc1CjtKuwc_gqVu
But using reverse engineering short links and get
https://onedrive.live.com/redir?resid=8F99649728BEB2F3!2727&authkey=!ADUKO0q7Bz-CpW4&ithint=photo%2cjpg
From here you can get a Onedrive direct download link for this file, check out my original post on this. If you need to share big files directly, you'll want to read it.
Reverse Engineer Shorted URL
Paste any shortened URL into to get original long URL.
Looks like the Microsoft URL Shortening is now active, in partnership with Bitly which has been rumored for awhile now.
For example, this OneDrive URL
shortened to a cute domain of 1drv.ms
For those that don't know, the Bitly default domain name is bit.ly
but this URL works as well.
So its solutions seems to be an URL domain alias.
NY Times uses Bit.ly as well (still working in 2017)
https://nyti.ms/2jHV1mn
https://bit.ly/2jHV1mn
17-Jan-17 Update
Microsoft apparently did not like this reverse engineering of its shortening service and now produces this obscure link
https://1drv.ms/i/s!AvOyviiXZJmPlSc1CjtKuwc_gqVu
But using reverse engineering short links and get
https://onedrive.live.com/redir?resid=8F99649728BEB2F3!2727&authkey=!ADUKO0q7Bz-CpW4&ithint=photo%2cjpg
From here you can get a Onedrive direct download link for this file, check out my original post on this. If you need to share big files directly, you'll want to read it.
Reverse Engineer Shorted URL
Paste any shortened URL into to get original long URL.
- Link Expander (http://www.linkexpander.com/) gets you a preview of link.